Resolving Open File Security Warning when Launching OpenInsight
 The standard multi-user deployment practice for OpenInsight involves executing OINSIGHT.exe across the network from a shared network folder. By default Windows distrusts network folder locations that haven’t been previously trusted and can’t be detected as part of the local intranet. This results in Windows displaying the Open File – Security Warning before launching the program.
The standard multi-user deployment practice for OpenInsight involves executing OINSIGHT.exe across the network from a shared network folder. By default Windows distrusts network folder locations that haven’t been previously trusted and can’t be detected as part of the local intranet. This results in Windows displaying the Open File – Security Warning before launching the program.
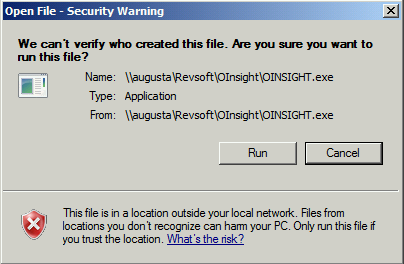
In this article we’ll cover 3 methods to prevent the Open File – Security Warning by configuring Windows to trust the shared OpenInsight network location.
Determine The OpenInsight Server Name
The first step to setup a trusted network location is to locate the server name where OINSIGHT.exe is being launched from. This is important because the name could be a:
- Short network name – \\augusta
- Fully qualified domain name (FQDN) – \\augusta.lan
- IP address – \\192.168.0.2
It’s important to setup the trusted network location using the name specified in the shortcut. Trusting the short network name but using a FQDN won’t work. Check your OpenInsight shortcut and locate the target server name that the shortcut points to. In our example the server is “\\augusta”.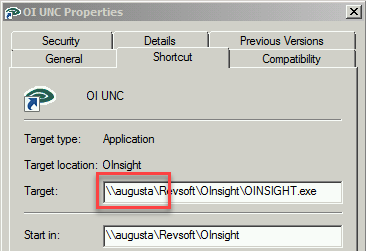
Option 1: Add the Path to OpenInsight as a Local Intranet Site
For networks with only a few users or workstations not part of the active directory network the easiest option is to add the OpenInsight server as a trusted intranet site on a per user basis. This is accomplished by following these steps on each user desktop running OpenInsight:
- Open the Internet Explorer browser and go to settings.
- Open the Security tab.
- Click Local intranet.
- Click the Sites button.
- Type your server name in the field Add this website to the zone as shown below.
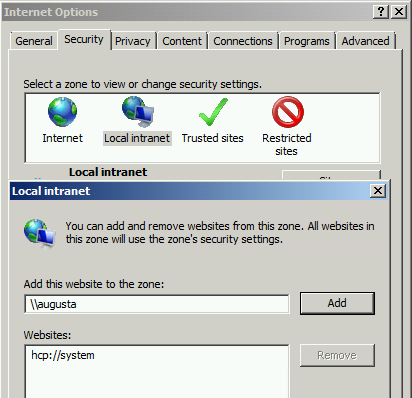
- Click Add when completed. The site will appear in the list formatted with the prefix ‘file://’
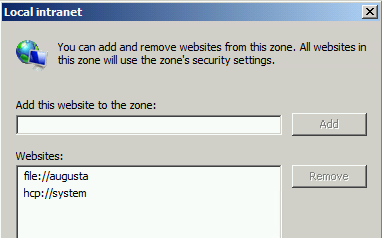
- Close the open settings window and try launching OpenInsight. The change should take effect immediately and OpenInsight should launch without displaying the file security warning. If not, log out and log back in or check the path.
Option 2: Using a Script to Add the OpenInsight Path as a Local Intranet Site
The OpenInsight server can also be added as a local intranet site by setting a registry entry. This is a more flexible version of the first option because it can be setup using:
- A network login script
- An OpenInsight Basic+ program
- A custom installer for your application
- A setting pushed over the network
Note: When used from an OpenInsight Basic+ program during your application launch the user will see at least one security warning message. After the warning message is acknowledged OpenInsight can launch, run your application’s start-up routine, and set the registry changes to prevent the user from seeing the security warning on subsequent launches.
To setup a new trusted site using the registry:
- Create a new registry path containing the name of the server. For example:
HKCU\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap\EscDomains\augusta
Where augusta is the name of the server used in this example. - In the path create a new registry key named file of type DWORD.
- Set the file registry key value of to be “1” to indicate the zone type is local intranet.
- Logout of your desktop and log back in to test the setting. Launching the OpenInsight shortcut should no longer display the file security warning.
The registry entry can be created from a batch or login script without any special tools using the command:
REG ADD "HKCU\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap\EscDomains\augusta" /v file /t REG_DWORD /d "00000001" /f
Substitute augusta with the name of your server.
Option 3: Using Group Policy to Configured the Local Intranet Site
Workstations managed through Active Directory can be configured by creating a group policy setting to trust network locations. This is especially important in Remote App or Citrix environments where users might never see their desktop. Setting up a group policy is beyond the scope of this article so please check with your network administrator on how to deploy these settings.
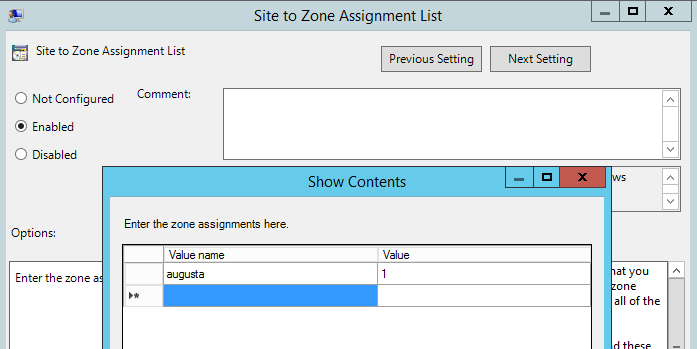
The Site to Zone Assignment List policy instructs Windows what zone a particular server should be placed in. Enable the group policy:
“User Configuration > Administrative Templates > Windows Components > Internet Explorer > Internet Control Panel > Security Page > Site to Zone Assignment List”
Add an entry into the policy zone list for the OpenInsight server by entering the server name as the Value name with a Value of 1 as shown below.
Then the policy is applied and propagated to users they should no longer see the security warning when launching OpenInsight.
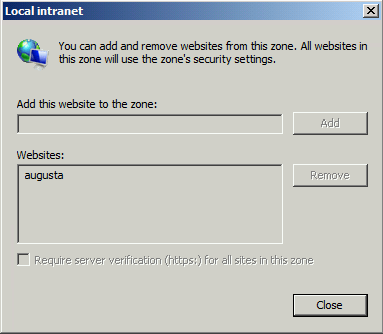
Troubleshooting Tip: If the policy does not prevent the security warning then check the workstation’s or remote desktop server’s IE ESC (Internet Explorer Enhanced Security Configuration) settings.When enabled, IE ESC can override the Site to Zone Assignment List and prevent the policy from applying. You can verify the policy has applied by checking the Local Intranet site list (see option 1). If the group policy has applied you should see your settings listed but will not be able to change the policy because it was applied through a group policy.
If your system administrator is unable to disable IE ESC for your users the policy Turn on automatic detection of intranet may help recognize some network locations as intranet sites. Lab testing revealed this setting usually detected short UNC paths like \\augusta as local intranet sites while paths using IP or FQDN addresses such as \\192.168.0.2 or \\augusta.lan continued to remain untrusted locations.
We hope this information helps you support your OpenInsight application and bring a greater level of trust to users by not showing unnecessary security warnings.
What if you are using mapped drives? i.e. n:\oi Site I’m at doesn’t appear to allow UNC paths for target path.
Mapped drives are basically aliases to UNC paths and Windows will resolve the mapped drive to a UNC path when deciding if it should trust a network location. For example, if your mapped drive is N:\ and you enter that into Internet Explorer’s Local intranet zone list as shown in option 1 then IE will translate N: to the server it points to when you click the Add button. So if N: points to \\myserver\share then the entry would translate to file://myserver when added to the list.
The UNC was more complicated then we thought got that to take but a group policy prevents adding trusted sites through IE apparently